One Address to Rule (Cyber)Security. What You Should Know About the New cyber.gov.pl Portal

Polish Cyber Defense: Between the Public Shield and the Hidden Sword
Polish cyber defense is a system with two faces. On one side, we have the new, official cyber.gov.pl website, designed to organize information chaos and offer free tools to citizens. On the other—in the shadows of offices and server rooms—an intelligence game is being played, in which Poland officially admits for the first time to possessing offensive "cyber weapons."
We hear about data leaks and phishing every day. The Ministry of Digital Affairs indicates that in 2025, the number of handled incidents rose to over 220,000 (an increase of over 100% YoY). In response to this threat, the state is building a security architecture that is far more complex than headlines suggest. We discover what this duality looks like in practice: from tools available to the average citizen, to a deterrence strategy rarely discussed in the news.
1. Two Faces of the System: Who Holds the Keys?
To understand Polish cybersecurity, one must recognize its intentional division into a public (civil) zone and a classified (state) zone. This is not just a matter of bureaucracy, but a fundamental defense strategy.
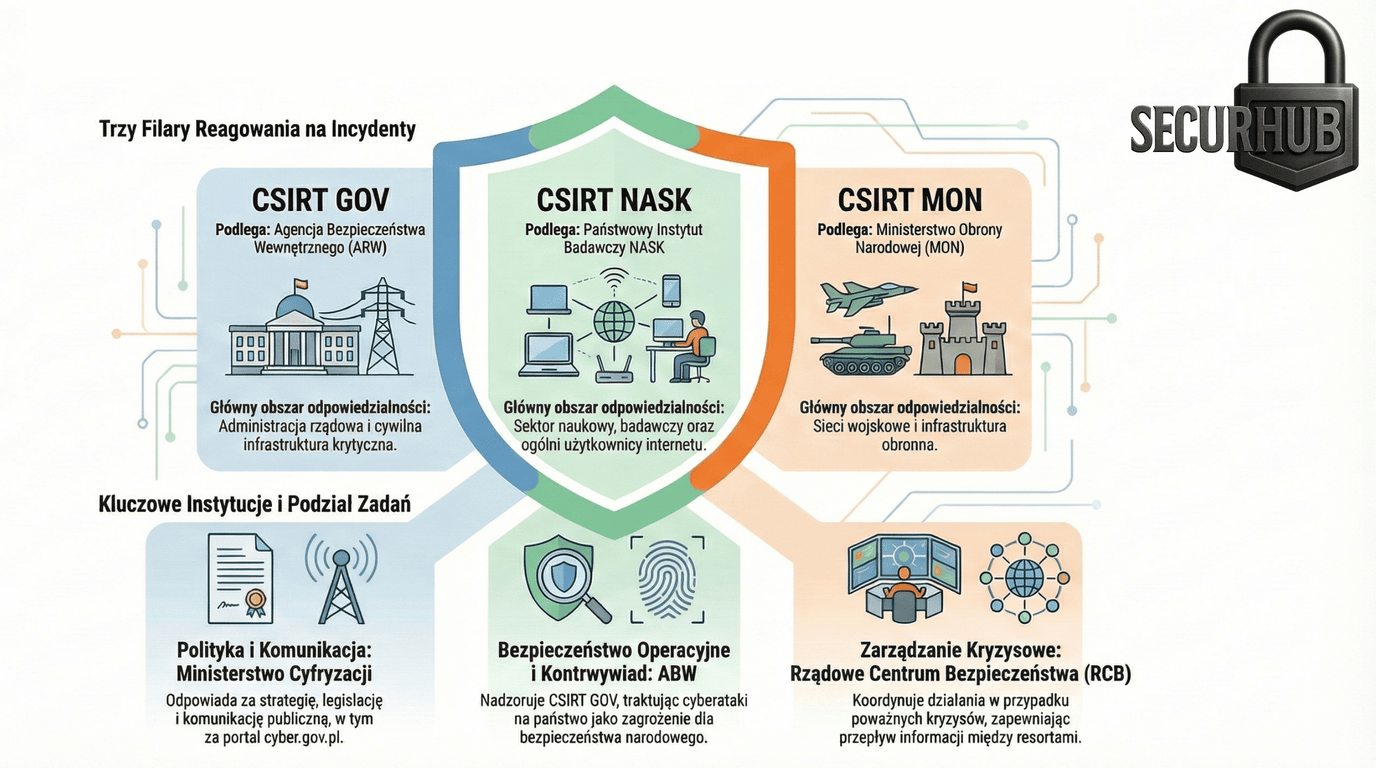
- The Public Layer (Ministry of Digital Affairs & NASK): This is the "bright side of the force." Its task is education, building social resilience, and providing tools like the
cyber.gov.plportal. It focuses on the cyber hygiene of citizens and companies. - The State Security Layer (CSIRT GOV & ABW): This is the state's "nervous system." This team reports not to the Ministry of Digital Affairs, but to the Head of the Internal Security Agency (ABW). Here, cyberattacks on critical infrastructure are not treated as technical glitches, but as potential acts of espionage or hostile actions by foreign states.
Key difference: By placing CSIRT GOV within the structures of counterintelligence (ABW), a serious incident in the state sphere triggers immediate investigative and attribution capabilities. This is a strategic advantage over purely civilian models.
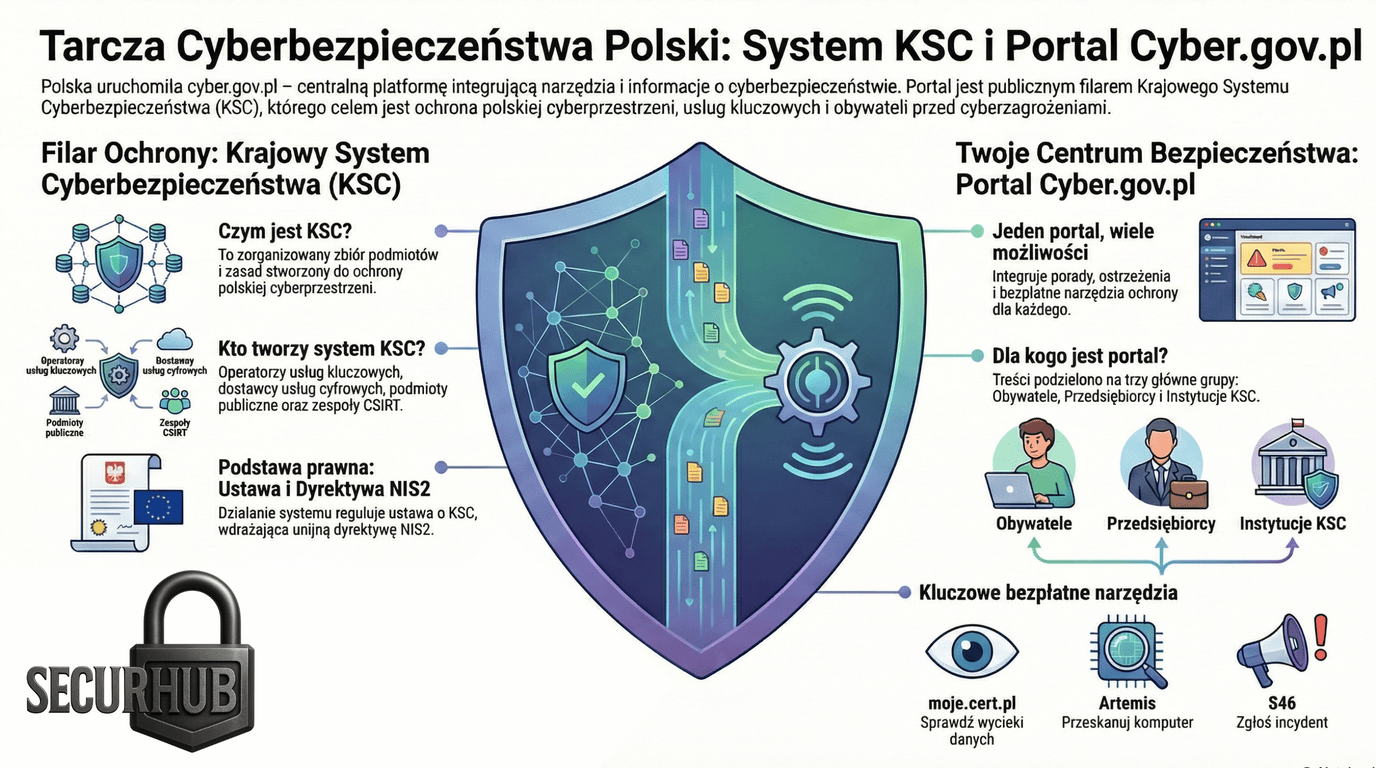
2. A Shield for the Citizen: What is cyber.gov.pl?
In response to the fragmentation of information regarding threats, the government launched the cyber.gov.pl portal. It is intended to be a "single address" allowing control over the chaos of disinformation and cyber threats. Instead of seeking help on forums, citizens and companies are to receive verified knowledge in one place.
The portal's creators divided it into zones to precisely target different audience groups:
| Target Group | What does the portal offer? |
|---|---|
| Citizens | Data protection guides, fraud warnings, education (e.g., how to create secure passwords). |
| Entrepreneurs | Knowledge on securing company infrastructure and business continuity. |
| Institutions (KSC) | Incident reporting tools, compliance guidelines for the NIS2 directive, and access to the S46 system. |
Free tools that actually work
The greatest value of the portal—appreciated even by skeptics—lies in the concrete, free tools developed by entities like CERT Polska, which allow users to move from theory to practice:
- moje.cert.pl: Check if your email and password have been leaked online.
- Artemis Scanner: A tool for scanning websites and servers in search of security vulnerabilities (for administrators).
- Safe Mail (Bezpieczna Poczta): Verification of suspicious messages and attachments.
3. A Crack in the Glass: Controversies and Criticism
Although cyber.gov.pl is a step toward organizing the ecosystem, the initiative has met with a cold reception from some experts. While the official narrative speaks of a "centralized platform," critics point to "minimalism and superficiality."
The main allegations concern:
- Functionality: Instead of integrating services, many tabs simply redirect to other, sometimes outdated government pages.
- Political Goal: Voices suggest the portal may serve to "build a facade of readiness" and manipulate public perception, providing an illusion of security while real problems lie deeper.
This dissonance between the promise of a "trusted platform" and allegations of it being a facade creates a trust gap that is dangerous during times of crisis.
4. From Defense to Attack: Poland's "Cyber Weapon"
The most surprising piece of the puzzle, rarely discussed in the context of free antivirus scanners, is the shift in Poland's war doctrine.
The Minister of Digital Affairs officially confirmed to Puls Biznesu that Poland possesses an offensive "cyber weapon." This is a fundamental change:
- A transition from a passive posture (defense) to active Integrated Deterrence.
- A public declaration of the capability to launch a retaliatory strike on an adversary's infrastructure in response to an attack on Polish networks (e.g., water or energy systems).
Poland sends a clear signal to allies and adversaries: we will not be just a shield. We are ready to impose real costs on an attacker, operating across the full spectrum of cyber conflict.
Summary: Where Are We Heading?
Polish cyber defense is a complex mechanism. On one hand, the state extends a hand to the citizen, offering basic protection tools via cyber.gov.pl—an initiative that is necessary, though still requiring refinement and integration (e.g., with the National Node). On the other hand, behind the scenes, ABW and CSIRT GOV are sharpening a digital sword, ready for offensive actions that most of us will never hear about.
The key to security in the coming years will not only be the strength of our secret cyber weapons but, above all, whether the public "shield" in the form of an aware society and efficient e-services proves not to be full of holes.
FAQ
What is cyber.gov.pl and who is it for?
It is a central government portal that aggregates cybersecurity information for citizens, entrepreneurs, and institutions. It is meant to be a "single address" for verified knowledge about threats and protective tools.
What free tools does the portal offer?
The most important ones are moje.cert.pl (checking for password and email leaks), Artemis Scanner (detecting vulnerabilities in websites), and Safe Mail (verifying suspicious messages).
Does Poland possess an offensive cyber weapon?
Yes. The Minister of Digital Affairs officially confirmed that Poland possesses offensive capabilities and can conduct a retaliatory strike on an aggressor's infrastructure in response to a cyberattack on critical Polish systems.
What is the difference between CSIRT GOV and CERT Polska?
CERT Polska (NASK) operates in the public and educational layer, providing tools for citizens and companies. CSIRT GOV reports to the ABW (Internal Security Agency) and protects the state's critical infrastructure, operating within the sphere of counterintelligence.
Aleksander
Sources
- Ministry of Digital Affairs launches cyber.gov.pl with key cybersecurity updates | Biznes PAP
- Poland has 'cyberweapons,' can strike back, digital minister says - Polskie Radio
- Cyber.gov.pl - Oficjalna strona rządowa ds. cyberbezpieczeństwa
- CERT Polska - Narzędzia i usługi
- ABW - Agencja Bezpieczeństwa Wewnętrznego
- Krajowy System Cyberbezpieczeństwa (KSC) - Gov.pl
- NIS2 Directive - European Commission
- Integrated Deterrence in Cybersecurity - NATO Review
- MC uruchomiło stronę cyber.gov.pl zawierającą najważniejsze komunikaty dotyczące cyberbezpieczeństwa
- Krzysztof Gawkowski: Mamy cyberbroń, pracujemy nad podatkiem cyfrowym, a w ciągu dwóch lat wprowadzimy e-rejestrację pojazdów
About the Author

Dyrektor ds. Technologii w SecurHub.pl
Doktorant z zakresu neuronauki poznawczej. Psycholog i ekspert IT specjalizujący się w cyberbezpieczeństwie.
Powiązane artykuły

NIS2 w Polsce 2025: 5 prawd, które zmienią wszystko w Twojej firmie - Kompletny przewodnik
Dyrektywa NIS2 to nie kolejne RODO - to rewolucja w cyberbezpieczeństwie z osobistą odpowiedzialnością zarządu i karami do 100 mln PLN. Odkryj, czy Twoja firma jest objęta regulacją i jak uniknąć dotkliwych sankcji.

Security Operations Center (SOC): Kompleksowy Przewodnik na 2026 | Budowa i Wdrożenie
Poznaj wszystko o Security Operations Center (SOC) - od budowy zespołu, przez technologie SIEM/XDR/SOAR, wymogi NIS2, modele wdrożenia, aż po przyszłość z AI. Praktyczny przewodnik dla CISO i menedżerów IT.

Cloud Security 2025: Najlepsze Praktyki dla AWS, Azure i GCP - Zero Trust, IAM, CSPM i Shared Responsibility Model
Błędna konfiguracja IAM to główna przyczyna incydentów w chmurze. Odkryj różnice między AWS, Azure i GCP w modelu Shared Responsibility, jak wdrożyć Zero Trust, unikać "toxic combinations" uprawnień, zabezpieczyć klucze CMK i zautomatyzować CSPM dla compliance NIS2.
Komentarze
Ładowanie komentarzy...